It Security


It Security Services Connection

Cyber Security And Executive Strategy Stanford Online

What Project Managers Need To Know About Cyber Security
It Security のギャラリー

Top Jobs In It Security It Security Job Designations Simpilearn

10 Signs You Should Invest In It Security Excalibur Communications

It Security Consultant Learning Paths Explored

It Security Vs Cyber Security What Is The Difference Logsign

How To Become An It Security Specialist Career Hq
Q Tbn 3aand9gct9zgofihqfieo8juo8ro68yxwhhptcbiazdw9ijtnnvciipyt2 Usqp Cau

It Security Law Enforcement Cyber Center

It Security

Taking Responsibility For Cyber Security In A Truly Virtual World
What Is State Of The Art In It Security Enisa
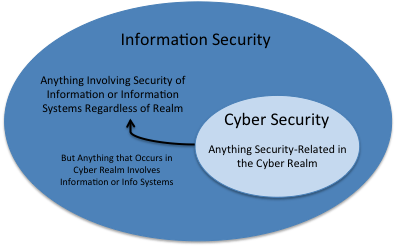
What Are The Different Types Of It Security Rsi Security

8 It Security Processes To Protect And Manage Company Data Process Street Checklist Workflow And Sop Software

Lack Of Internal It Security Expertise Requires Connected Threat Defense

Why Is Cyber Security Important In 19 Securityfirstcorp Com

What Is An It Security Audit Cheeky Munkey
Infographic It Vs Cyber Security The Main Differences Cybint

Why Multiple Layers Of Cyber Security Is Essential Lms Group
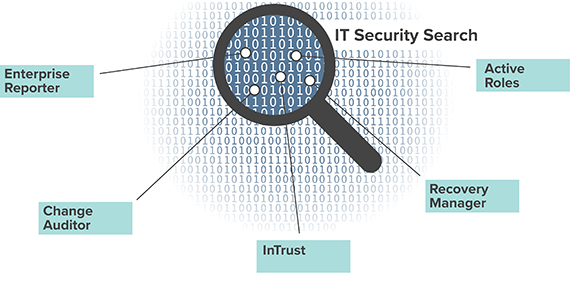
It Forensics And Security Auditing Software

It Compliance Vs It Security What S The Difference Bmc Blogs

12 Things Every It Security Professional Should Know Cso Online

Matrix42 On Why Ueba Offers A Smart Approach To Enhanced It Security Intelligent Ciso

Bank It Security Can Still Learn From 15 Top Takeaways Part 1 Thales Blog

Infographic Here Are 10 Reasons Why Cyber Security Needs To Be Top Priority In 19 Link11
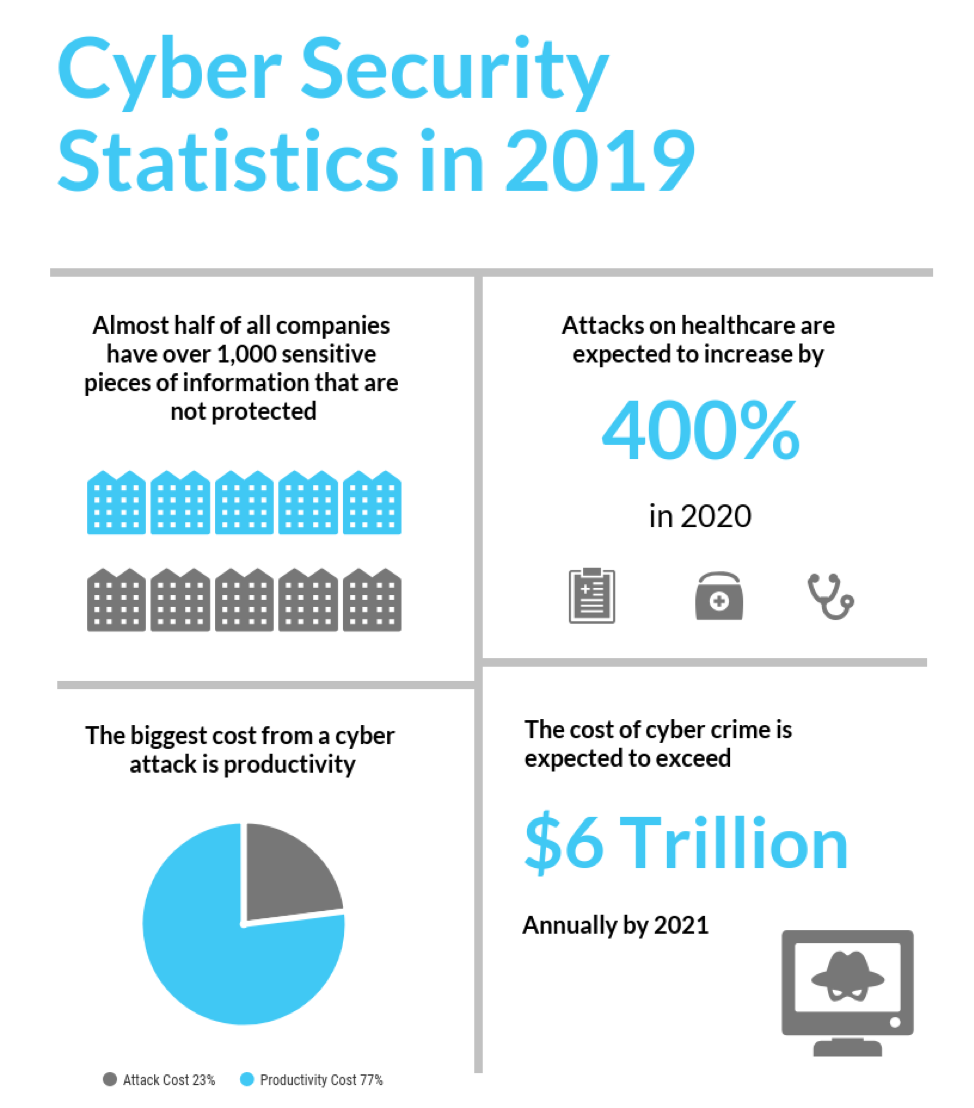
How Techology Is Revolutionizing It Security Software
Q Tbn 3aand9gct9zgofihqfieo8juo8ro68yxwhhptcbiazdw9ijtnnvciipyt2 Usqp Cau

Cybersecurity Atmosphere Chicago Cybersecurity

The Rising Costs Of Cybersecurity Breaches Why It Security Is Doomed To Fail

10 Common It Security Risks In The Workplace

It Security Vs Cybersecurity Cybersecurity Comptia
It Security Party Tricks Cybersecurity Insiders

Bai Security Vulnerability Scanning It Security Assessment Vulnerability Management Vulnerability Assessment Tools Social Engineering Attacks Red Team Assessment It Cyber Security Risk Assessment What Is Social Engineering 847 410 8180 We

Strong Growth In The It Security Market In Germany Mybusinessfuture

It Security Coordinator Sign Up To Freelance

A Cto Guide Cyber Security Best Practice Tips Information Age

It Security Policy Development Infosight

Cyber Security Strategy Solutions Conet De
Q Tbn 3aand9gcqotybmwejv42cihkardepkjad0 Ikrhviknqwrmzittjv3c4gb Usqp Cau

The Top Ai Cyber Security Companies Information Age

What Is Cyber Security Definition Types And User Protection Kaspersky

Methods For Easing Your Top Cyber Security Challenges Channel Futures

How To Write An It Security Engineer Job Description Cso Online

How Much Does A Cyber Security Specialist Make

Ship Cyber Security The Classnk Approach To Securing Onboard Systems

Businesses Beware Top 5 Cyber Security Risks Connected It Blog

Managed Security Services Irvine Ca Cybersecurity Vology

It Security Iowa State University

5 Must Implement Cyber Security Strategies For 19 Coffee With Cis Latest News Articles

The Role Of An It Security Professional Technojobs Uk

How To Protect Your Practice From Cyber Attacks With Cyber Security

4 Easy Steps How To Conduct It Security Audit Of Your Own Company

Cybersecurity Company I Affordable And Effective Cybersecurity Solutions Compliance And Consulting Services

The Importance Of Changing Your Cyber Security Mindset It World Canada News

Who Needs Cyber Security

It Security Policy Template Free Privacy Policy

7 Hidden Benefits Of It Security Compliance For Your Business

Macomb Community College It Network Security Professional Cybersecurity

Council Post 10 Cybersecurity Protocols Every Tech Professional Should Follow

Cto Vs Ciso Who Should Have Ultimate Responsibility For Cyber Security

How To Practice Cybersecurity And Why It S Different From It Security Cso Online

Cyber Security Training In Houston Cyber Security Certification Course
What Is Cyber Security Cybersec Threats Strategy Imperva

How To Better Integrate It Security And It Strategy Cio

Cloud Cape It Security Penetration Testing Vulnerability Management Managed Cloud

10 Cyber Security Tips Fro Small Business Pentucket Bank

It Security Solutions Itg Information Technology Group

It Security Consulting Cyber Security Experts And Best Practices Sophos

Information Infrastructure Security Management Mindtree

It S Time To Distinguish Information Security From It Security Nucleus Cyber

Cyber Security Insurance On The Rise Aws Insurance Company

What Is Cyber Security A Beginner S Guide Rasmussen College

What Is An It Security Audit The Basics Varonis

4 It Security Best Practices Smbs Need To Adopt Immediately Bytestart
1

Is A Cyber Security Degree Worth It The Facts You Can T Ignore Rasmussen College

Cybersecurity Vs Information Security Is There A Difference Cloud Academy

Strong Growth In The It Security Market In Germany Mybusinessfuture

12 Top Tips For Cyber Security Context Information Security

It Security Nasa

It Security Vulnerability Vs Threat Vs Risk What Are The Differences Bmc Blogs

Creating A Covid 19 Cyber Security Plan Connected It Blog

Why Segregation Of Duties Is Crucial For It Security Network Security

The Rising Pressure To Invest In More It Security Talent Talent Germany
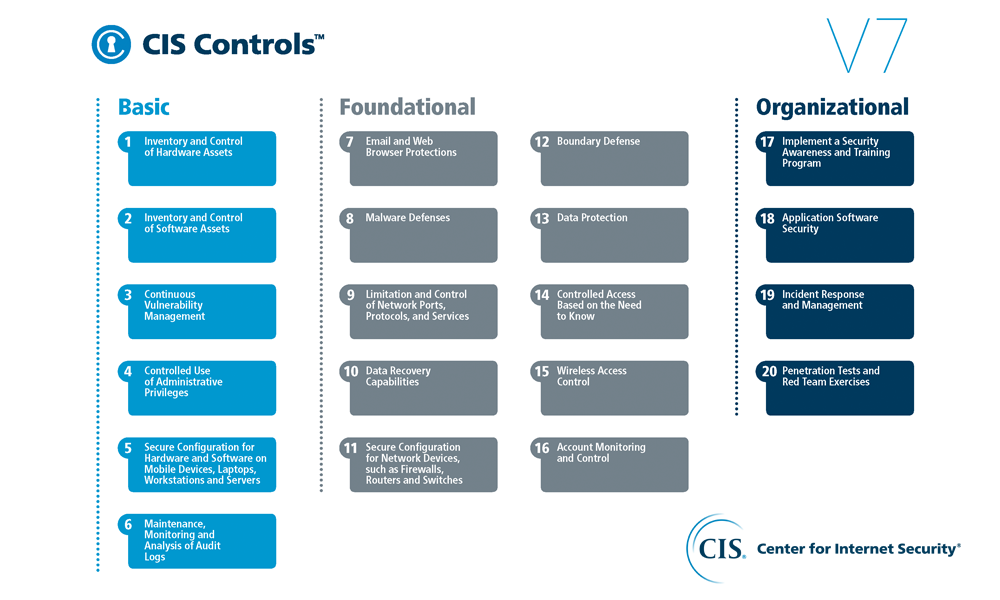
It Cyber Security Discovery Lansweeper It Discovery Software

No Shortcuts To Effective Cyber Security Amp Information Systems

Cybersecurity Audit Checklist Reciprocity

It Security Risk Assessment Methodology Securityscorecard
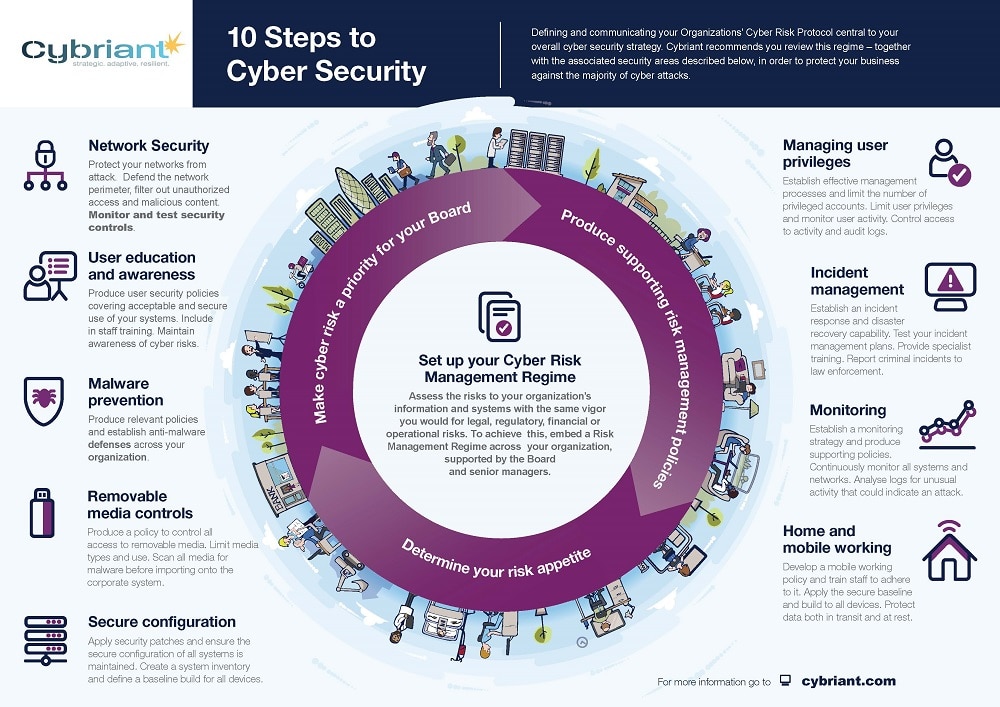
10 Steps To Define Your Cyber Security Strategy Cybriant

S2oisd7drqahcm

Infographic 12 Top Tips For Cyber Security Context Information Security

3 Essential Components Of Your It Security Roadmap

Few Execs Believe Healthcare It Security Tech Will Be Disruptive

Top 10 It Security Stories Of 18

Cyber Security Firm Skout To Create 30 Jobs As It Opens European Hq In Laois

Cyber Security Specialist Job Description And Salary Fieldengineer

Information Security Dasher S Hierarchy Of It Security Needs Dasher

Why Is Cyber Security Important It Company Birmingham

It Security Refresh The Cyber Defense Matrix No Jitter

What Is It Security Information Technology Security Cisco

Cisco Network And It Security Solutions Cisco

Cyber Security Monitoring Network Monitoring Redscan

Industrial Cyber Security Why It Ot Collaboration Is No Longer An Option But A Necessity



